Introduction

Cybersecurity is important for many public and private companies and organizations. It is considered as the main firewall for the entities’ various sensitive data. If this firewall collapses or gets penetrated, a company or organization becomes an easy target for criminal entities.
The Kingdom of Saudi Arabia aims to create a safe and reliable Saudi cybersecurity arena that enables development and prosperity on a local scale.
To contribute effectively to the advancement of the Kingdom internationally in specific fields, such as cybersecurity, and to support the realization of national targets, the Saudi Electronic University, represented by the Cybersecurity Center, launches the first cybersecurity camp under the title of “CyberGate Camp & Competition”.
The Camp
CyberGate Camp aims to develop the skills of national talents of university students who are qualified to work in the field of cybersecurity, through specialized online workshops offered on a virtual platform and delivered by experts and specialists, in order to raise social awareness and polish technological skills in the field of cybersecurity. The training program includes tasks for creating innovative projects and solutions to enhance organizations’ and societies’ cybersecurity. The best projects are nominated to participate in a competition under specific standards. These standards include: idea uniqueness, AI application level, presentation quality, and project applicability.
Learning Outcomes:
Govern cybersecurity.
Evaluate social engineering & phishing risks.
Raise awareness of ethical hacking.
Identify cybersecurity challenges and solutions.
Recognize cybersecurity concepts and applications.
Demonstrate the proper approach to conduct digital foronsics investigation.
The Competition
The training program includes tasks for creating innovative projects and solutions to enhance organizations’ and societies’ cybersecurity. The best projects are nominated to participate in a competition under specific standards. These standards include: idea uniqueness, AI application level, presentation quality, and project applicability. Participants compete for winning one of the first three ranks with an award of 6 thousand SAR in total.
Awards
First 3000 SR
Second 2000 SR
Third 1000 SR
Program Stages
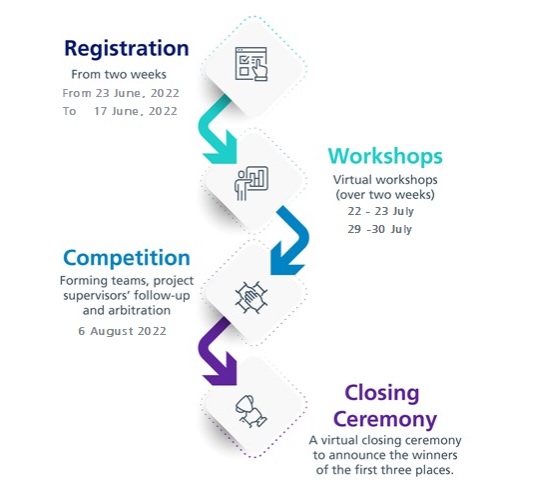

Workshop Outline
Specialized online workshops via virtual platform, delivered by experts and specialists in this field.
Cybersecurity concepts and applications.
Cybersecurity challenges and solutions.
Ethical Hacking.
Social engineering and phishing risks.
Cybersecurity Governance.
Digital fronsics.
Cloud Computing.
IoT.
First Day Workshop
|
Friday, July 29, 2022 4:00 to 6:40 PM *Sessions access passwords will be sent 30min before the start of the sessions* |
|
|
Opening 4:00 – 4:10 PM |
Introduction to CyberGate Dr. Hamdan Alzahrani Cybersecurity Center Supervisor Saudi Electronic University |
|
First Session 4:10 – 5:10 PM |
Cybersecurity Concepts and Applications Eng. Abdulrahman Al-Nimari Cybersecurity consultants Cyber Influencer Award 2022
Topics: - Road Map to study cybersecurity. - Requirements to study cybersecurity. - Cybersecurity Career. - Resources to study cybersecurity. |
|
Break 20 minutes (5:10 to 5:30 PM) |
|
|
Second Session 5:30 – 6:30 PM |
Cybersecurity Challenges and Solutions Ms. Bushra Alsulayyim College of Computing and Informatics Saudi Electronic University Cybersecurity consultants, Auditing, Eastern Health Cluster Topics: - Cybersecurity challenges in 2022. - Remote Working. - Cybersecurity skills gap. - Lack of cybersecurity culture. - Cyber Attacks: In the Healthcare and educational sectors. - Supply chain attack. - AI and Machine-Learning: a blessing or a curse for Cyber Security? |
|
Closing Q&A (6:30 to 6:40 PM) |
|
Second Day Workshop
|
Saturday , July 30, 2022 4:00 to 6:40 PM *Sessions access passwords will be sent 30min before the start of the sessions* |
|
|
Opening 4:00 – 4:10 PM |
Introduction to CyberGate Dr. Hamdan Alzahrani Cybersecurity Center Supervisor Saudi Electronic University |
|
First Session 4:10 – 5:10 PM |
Social Engineering and Phishing Risks Dr. Fahad Alodayani Cybercrime consultant Vice Dean - Computing and Information Technology, King Abdulaziz University -Rabigh Associated Professor
Topics: - What is social engineering? - Components of social engineering. - Risks of social engineering. - Social engineering prevention. |
|
Break 20 minutes (5:10 to 5:30 PM) |
|
|
Second Session 5:30 – 6:30 PM |
Digital Forensics ENG. Badar Alharbi SADEED digital forensic Lab service
Topics: - Data collection techniques. - Tools for data collections. - Data analysis techniques. - Tools for data analysis. |
|
Closing Q&A (6:30 to 6:40 PM) |
|
Third Day Workshop
|
Friday, August 5, 2022 4:00 to 6:40 PM *Sessions access passwords will be sent 30min before the start of the sessions* |
|
|
Opening 4:00 – 4:10 PM |
Introduction to CyberGate Dr. Hamdan Alzahrani Cybersecurity Center Supervisor Saudi Electronic University |
|
First Session 4:10 – 5:10 PM |
Cloud Computing Dr. Sultan Almakdi Assistant Professor of Cybersecurity Vice Dean of IT at Najran University
Topics: - Introduction to cloud computing. - Data Processing and storing at Cloud. - Security risks of cloud computing. - Examples of data breaches that can happen. - Data leakage prevention. - Encryption, Pros and Cons. |
|
Break 20 minutes (5:10 to 5:30 PM) |
|
|
Second Session 5:30 – 6:30 PM |
IoT Dr. Badr Alsamani Dean of Information Technology at Al Imam Muhammad Ibn Saud Islamic University
Topics: - IoT enabling opportunities. - IoT and security concerns. - IoT and privacy concerns. |
|
Closing Q&A (6:30 to 6:40 PM) |
|
Fourth Day Workshop
|
Saturday, August 6, 2022 4:00 to 6:40 PM *Sessions access passwords will be sent 30min before the start of the sessions* |
|
|
Opening 4:00 – 4:10 PM |
Introduction to CyberGate Dr. Hamdan Alzahrani Cybersecurity Center Supervisor Saudi Electronic University |
|
First Session 4:10 – 5:10 PM |
Cybersecurity Governance Eng. Hashem Al-Azizi Cybersecurity GRC
Topics: - Introduction to cybersecurity governance. - Importance of cybersecurity governance. - Proposed method to carry on cybersecurity governance. |
|
Break 20 minutes (5:10 to 5:30 PM) |
|
|
Second Session 5:30 – 6:30 PM |
Ethical Hacking Dr. Dheyaaldin Alsalman Assistant Professor of Cybersecurity Dar Al-Hekma University
Topics: - Hacking concepts. - Reconnaissance techniques. - Vulnerability scanning tools. - Exploitation tools. - Potential projects. |
|
Closing Q&A (6:30 to 6:40 PM) |
|
Registration Terms
The participant should have knowledge in one of the programming languages.
The participant must attend all the camp workshops and submit all required work in order to be nominated for the competition.
The participant must attend the entire camp in order to receive the camp completion certificate.
The participant must be at least 18 years old.
The participant should have basic knowledge of the English language.
Register Now
Please click here